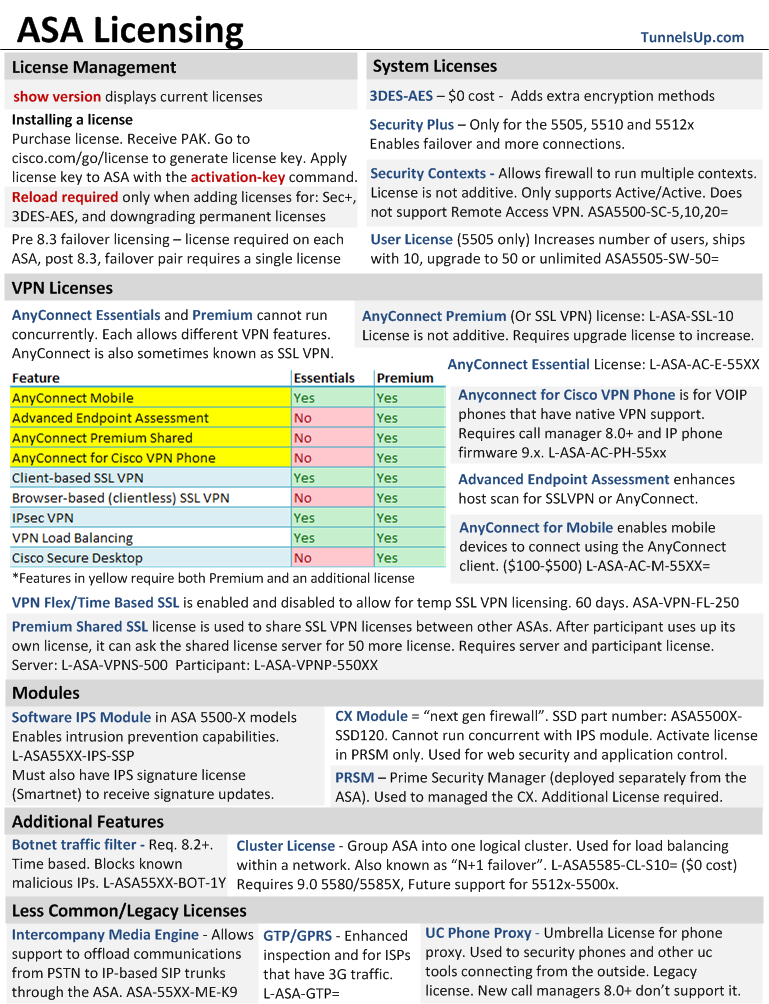
Cisco Asa Security Plus License Crack
This platform has a Base license. Failed to retrieve flash permanent activation key. Did I somehow kill my Security Plus licensing when I did the erase flash? If so how do I recover it? Ciscoasa# sh activation-key. Serial Number: JMXXXXXXHU. Running Permanent Activation Key:. Cisco ASA 5505 Security Plus license provides stateless active/standby high availability, dual ISP support, DMZ support, VLAN trunking support, and increased session and IPSec VPN peer capacities. Cisco ASA 5505 Security Plus License is rated 4.2 out of 5 by 93.
Two vulnerabilities in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to elevate privileges to the root user or load a malicious library file during execution.
The vulnerabilities are not dependent on one another; exploitation of one of the vulnerabilities is not required to exploit the other vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other vulnerability.
Details about the vulnerabilities are as follows.
Cisco Adaptive Security Appliance Smart Tunnel Privilege Escalation Vulnerability
A vulnerability in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to elevate privileges to the root user. This privilege escalation happens on a client device that attempts to establish a smart tunnel connection with the Cisco ASA. The escalation does not occur on the ASA itself.
The vulnerability occurs because the Cisco ASA smart tunnel creates local system files on the client device with file permissions that are not restrictive enough. In addition, the ASA smart tunnel does not validate the system commands in these local system files before executing them. An attacker could exploit this vulnerability by running a malicious script on the client device when a valid user is establishing the Cisco ASA smart tunnel connection. A successful exploit could allow the attacker to elevate privileges to root on the client machine without the user's knowledge. The attacker needs valid device credentials on the local client device to exploit this vulnerability.
The CVE ID for this vulnerability is: CVE-2019-1944
Cisco Adaptive Security Appliance Smart Tunnel Library File Load Vulnerability
A vulnerability in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to overwrite specific system files, which could then be loaded and executed during smart tunnel connection establishment. The attacker could take these actions on the client device that is attempting to establish the smart tunnel connection with the Cisco ASA and not on the ASA itself.
The vulnerability occurs because the Cisco ASA can write files to specific locations on the file system, and the smart tunnel functionality does not validate the integrity of system files that load during execution. An attacker could exploit this vulnerability by creating a malicious system file and writing it to a specific location on the file system when a valid user is establishing the Cisco ASA smart tunnel connection. A successful exploit could allow the attacker to cause the smart tunnel to load a malicious executable. The attacker needs valid device credentials on the local client device to exploit this vulnerability.
The CVE ID for this vulnerability is: CVE-2019-1945
Two vulnerabilities in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to elevate privileges to the root user or load a malicious library file during execution.
The vulnerabilities are not dependent on one another; exploitation of one of the vulnerabilities is not required to exploit the other vulnerability. In addition, a software release that is affected by one of the vulnerabilities may not be affected by the other vulnerability.
Details about the vulnerabilities are as follows.
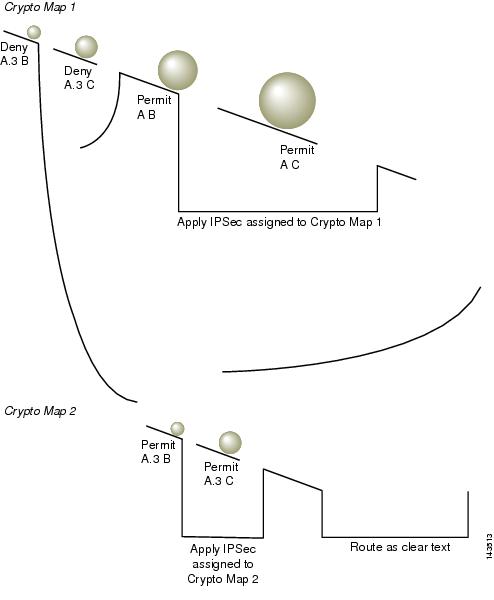
Cisco Adaptive Security Appliance Smart Tunnel Privilege Escalation Vulnerability
A vulnerability in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to elevate privileges to the root user. This privilege escalation happens on a client device that attempts to establish a smart tunnel connection with the Cisco ASA. The escalation does not occur on the ASA itself.
The vulnerability occurs because the Cisco ASA smart tunnel creates local system files on the client device with file permissions that are not restrictive enough. In addition, the ASA smart tunnel does not validate the system commands in these local system files before executing them. An attacker could exploit this vulnerability by running a malicious script on the client device when a valid user is establishing the Cisco ASA smart tunnel connection. A successful exploit could allow the attacker to elevate privileges to root on the client machine without the user's knowledge. The attacker needs valid device credentials on the local client device to exploit this vulnerability.
The CVE ID for this vulnerability is: CVE-2019-1944
Cisco Asa Security Plus License Crack 2017
Cisco Adaptive Security Appliance Smart Tunnel Library File Load Vulnerability
A vulnerability in the smart tunnel functionality of Cisco ASA could allow an authenticated, local attacker to overwrite specific system files, which could then be loaded and executed during smart tunnel connection establishment. The attacker could take these actions on the client device that is attempting to establish the smart tunnel connection with the Cisco ASA and not on the ASA itself.
Asa 5520 Vpn Plus License
The vulnerability occurs because the Cisco ASA can write files to specific locations on the file system, and the smart tunnel functionality does not validate the integrity of system files that load during execution. An attacker could exploit this vulnerability by creating a malicious system file and writing it to a specific location on the file system when a valid user is establishing the Cisco ASA smart tunnel connection. A successful exploit could allow the attacker to cause the smart tunnel to load a malicious executable. The attacker needs valid device credentials on the local client device to exploit this vulnerability.
Security Plus Study Guide
The CVE ID for this vulnerability is: CVE-2019-1945